Library Management System Capstone Project Document
Objective
The target of this project is to develop a utility that may automate the entire process of a library. The software program that may be developed ought to have services like Add / Delete Members, Add / Delete Books, Difficulty & Return. The application should be secured, in addition to with restricted entry.
The main requirement of the project would be the ease of use, moreover being probably the most environmentally friendly and efficient device for the aim. The application should be user-friendly. It ought to be sturdy and scalable.
An automatic solution can be very helpful to the group, as it will deliver construction to the entire course in order that it may be traced for any type of question. Additionally, an automated solution will result in optimum utilization of the available resources, lowering duplication of effort, growing effectivity and minimizing time-delays.
Following are the main objectives of computerization:
- To offer services to all the workers for the problem, return & search and so on.at one place.
- To enhance coordination in staff.
- To reduce paper filling work
- To reduce the risk of fraud.
- To reduce the chances of information leaking.
Scope
Members
- Facility for SEARCH of Books based on Accession Number, Title, Author, Subject, Keyword.
- Facility for ISSUE / RETURN Books.
- Facility for RENEWAL of Books.
For Library Staff
- Automatic installation
- Simple and intuitive GUI for performing all functions
- Short-cut keys and point-and-click operation.
- Security features like access control using passwords and login-i.d.
- Automatic calculation of late-fee.
- Facility to ADD / DELETE Members, Library Staff & Books and Maintain an easy record of all these.
Problems With The Current System
- Issue / Return a book from/to the library is a cumbersome process. Various details need to be remembered by the staff members. It is very difficult to keep a track of all the members/books manually.
- Maintenance of the record of each member/book is a very tedious job. A large number of human efforts are required to keep a track of members who have issued a book, who has returned a book and which book is issued/returned.
- Modifying the details of members or books is a very tedious job if done manually.
Advantages
The benefits of the proposed software are as follow:
Reliability
The application would efficiently store all the information related to the various processes in the system and output the relevant information.
Availability
The appliance could be available to all the staff of the organizations with an authorized entry to the workstations and people who are subject to the authorization permissions.
Security
The system would have ample safety checking by means of the authentication of the users. The reports would solely be available to the staff of the library as per their particular requirements.
Cost Reduction
It can be achieved by minimizing the use of the stationary for reports. Soft copy of all the reports. Soft copy of all the reports can be viewed and hence reducing the need for the hard copy.
Project Management System
Project management involves the planning, monitoring, and control of the people, process, and events that occur as software evolves from a preliminary concept to an operational implementation. Effective software project management focuses on the four principles: people, product, process, and project.
The people
Software engineering institute has developed a people management capability maturity model (PM-CMM). The people management maturity model defines the key practice areas for software people like recruiting, selection, performance management, training, compensation, carrier development, organization, and work design, and team/culture development.
The product
Before a project can be planned, product objectives and scope should be established, alternative solutions should be considered and technical and management constraints should be identified. Scope identifies the primary data, functions, and behaviors that characterize the product.
The process
A software process provides the framework from which a comprehensive plan for Software development can be established.
Framework activities – are populated with tasks, milestones, work products, and Quality assurance points. These activities characterize the software product and the project team.
Umbrella activities – i.e. software quality assurance, software configuration management, and measurement overlay the process model.
The project
Planned and controlled software projects are conducted to manage complexity. To avoid project failure, the project manager must avoid a set of common warning signs, understand critical success factors and develop a common sense approach for planning, monitoring and controlling the project.
Software Process Model
A process model for software engineering is chosen based upon:-
- Nature of the Project.
- Methods and Tools to be used.
- Control and desired deliverables.
The process model, we have chosen to develop this software is a Linear Sequential Model
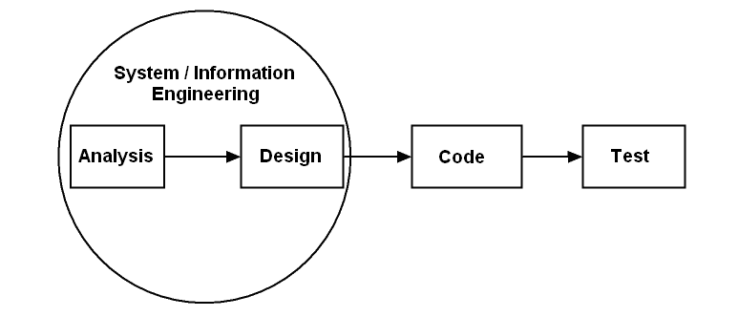
Linear Sequential Model suggests a systematic, sequential approach to software development that begins at the system level and progresses through analysis, design, coding, testing, and support.
Linear Sequential Model approach has the following phases:-
Software requirements analysis
In this, software engineer understands the nature of a program to be built, he must understand the information domain for the software as well as the required function, behavior, performance and interface. Requirements for both the system and the software are documented and reviewed with the customer.
Design
It has four distinct attributes of a program: data structure, software architecture, interface representations, and procedural detail. It is documented and becomes part of the software.
Code generation
The design must be translated into a machine-readable form which is done by code generation.
Testing
It focuses on the logical internals of the software, ensuring that all the statements have been tested, and on the functional externals; that is conducting a test to uncover errors and ensure that defined input will produce actual results.
The Software model used is LINEAR SEQUENTIAL MODEL because of the following reasons:-
- The project being small demands a systematic and sequential approach to software development i.e. system engineering, software requirement analysis, design, code generation, testing, and support occur in sequence.
- All requirements for the project have been explicitly stated at the beginning. There is a very little scope of customers’ deviation from current requirements, coding, and testing after detailed analysis are much easy.
- The structure is less complex and less innovative with less need for iteration.
Support
This is a phase when software will undoubtedly undergo changes after it is delivered to the customer. The change will occur because errors have been encountered because the software must be adapted to accommodate changes in its external environment, or because the customer requires functional or performance enhancements. Software support/maintenance reapplies each of the preceding phases to an existing program rather than a new one.
Team Structure
The “best” team structure depends on:-
- The management style of the organization.
- The number of people who will populate the team and their skill levels, and
- The overall problem difficulty.
The three generic team organizations are:
Democratic decentralized (DD)
This software engineering team has no permanent leader. Process coordinators are appointed for a brief period after which changed by others who might coordinate completely different duties. Communication amongst team members is horizontal.
Controlled decentralized (CD)
This software engineering team has a defined leader who coordinates specific tasks and secondary leaders that have responsibility for subtasks. Problem-solving stays a group activity. Communication amongst subgroups and individual is horizontal.
Controlled centralized (CC)
Top- level problem solving and internal team coordination is managed by a team leader. Communication between the leader and team members is vertical.
The team structure used in our project is DEMOCRATIC DECENTRALISED. The team comprises of two members:-
- Shobhna(7840)
- Megha Jain(7837)
Decentralized teams generate better options and have a larger probability of success when engaged in completely different issues. DD team construction is greatest applies to applications with low modularity.
Based on the difficulty of the problem to be solved relatively low modularity of the project and high volume of the communication required a democratic decentralized team structure is proposed. This software engineering team has no permanent leader. Rather, “activity coordinators are appointed for a brief period after which changed by others who might coordinate completely different duties.” Problem-solving is a group activity. Communication among team members is horizontal. The decentralized team generates more and better solutions than individuals. Therefore such teams have a greater probability of success when working on difficult problems.
A decentralized structure can be applied to both simple and difficult problems, but it is best applied in case of difficult problems. These team structures result in high morale, therefore good for teams that will be together for a long time. The decentralized team structure is best applied to the problem with relatively low modularity because of the higher volume of communication needed. These teams require more time to complete a project and at the same time be best when high sociability is required. In these teams, team members have trust in each other, distribution of skills must be appropriate to the problem and they share a common goal.
Software Project Scheduling
WHAT IS IT?
Software program Scheduling is an activity that distributes estimated effort throughout the deliberate mission by allocating the trouble to a particular software program engineering duties.
If you develop a schedule, compartmentalize the work, characterize the duty interdependencies, allocate time and effort to every job, defined duties for the work to be achieved, and defined outcomes and milestones.
WHY IS IT IMPORTANT?
With a view to constructing a fancy system, many software program engineering duties happen in parallel, and the results of work carried out throughout one job could have a profound impact on work to be performed in one other job. These interdependencies are very obscure without a schedule. It’s additionally just about inconceivable to progress on an average or giant software program mission without a detailed schedule.
Timeline Chart
Introduction
When creating a software project schedule, the planner begins with a set of tasks. If automated tools are used, the work breakdown is input as a task network or task outline. Effort, duration and start date are then input for each task outline. In addition, tasks may be assigned to specific individuals.
As a consequence of this input, a Timeline Chart is generated. It enables you to determine what tasks will be conducted at a given point in time.
| S. No. | TASK | Date of Start | Date Of Completion |
|
1 |
Requirement gathering & Analysis | ||
| 1.1 | Library Staff | 02.01.2008 | 04.01.2008 |
| 1.2 | Members (Students & Teachers) | 06.01.2008 | 09.01.2008 |
| 1.3 | Search | 11.01.2008 | 14.01.2008 |
| 1.4 | Issue & Return | 16.01.2008 | 23.01.2008 |
| 1.5 | FPA Calculation | 25.01.2008 | 31.01.2008 |
| 1.6 | Data Dictionary | 02.02.2008 | 05.02.2008 |
| 1.7 | ERD | 07.02.2008 | 11.02.2008 |
| 1.8 | DFD | 15.02.2008 | 21.02.2008 |
| 2 | Design | ||
| 2.1 | Data Design | 24.02.2008 | 29.02.2008 |
| 2.2 | Architectural Design | 10.03.2008 | 15.03.2008 |
| 2.3 | Interface Design | 17.03.2008 | 23.03.2008 |
Risk Analysis & Management
Risk analysis and management are a series of steps that help a software team to understand and manage uncertainty. Many issues can plague a software project, a danger is a possible downside which may occur or may not.
Risk Identification
This is the first step for recognizing what can go wrong.
Next, every risk is analyzed to find out the probability that it’ll happen and the harm that it’ll do if it does happen. As soon as this data is established, risks are ranked by their chance and impression. Lastly, a plan is developed to handle these risks with excessive chance and impression.
It’s Work Product
Risk mitigation, monitoring, and management (RMMM) plan or a set of risk information sheets are produced.
Categories Of Risk
Project Risks
They threaten the project plan. They establish potential budgetary, schedule, personnel, useful resource, customized potential, and necessities drawback and there influence on a software program project. They could end in a delay in project schedule and cost.
Technical Risks
They establish potential design, implementation, interface verification, and maintenance. They threaten the standard and timeliness of software program.
Business Risks
They often jeopardize the project or the product & include market risk, strategic risk, management risk, and budget risk.
Risk Mitigation Plan
All risk analysis activities presented to this point have a single goal to assist the project team in developing a strategy for dealing with risk.
Issues:
- Risk avoidance
- Risk monitoring
- Risk management and contingency planning
Steps taken are:
- Meet with current staff and check cause for problems
- Mitigate causes which are under control before the project starts
- Presume turnover will occur develop plans
- Conduct peer reviews
Risk Strategies
Reactive
A Reactive Strategy monitors the risk project for likely risk and set aside resources to deal with them, should they become actual problems. Software team does nothing about risks until something goes wrong.
Proactive
The proactive strategy begins long before technical work is initiated. Potential risks are identified, their probability impact is assessed, and they are ranked by importance.
Complexity Table
Input Screen
| S. No | Screen Name | No. of fields | No. of files | Complexity |
| 1. | Add Member | 10 | 1 | Average |
| 2. | Add Book | 8 | 1 | Average |
| 3. | Issue With Member ID | 3 | 3 | Average |
| 4. | Issue With Acc. No. | 3 | 3 | Average |
| 5. | Issue | 4 | 3 | Average |
| 6 | Return | 2 | 2 | Low |
| 7. | Return after Fine | 1 | 3 | Low |
Output Screen
| S. No | Screen Name | No. of fields | No. of files | Complexity |
| 1. | Member Search | 11 | 2 | Average |
| 2. | Member’s Detail | 11 | 2 | Average |
| 3. | Book Search | 9 | 1 | Average |
| 4. | Book’s Detail | 8 | 1 | Average |
Query Screen
| S. No | Screen Name | No. of fields | No. of files | Complexity |
| 1. | Log-in | 2 | 1 | Low |
| 2. | Delete Member | 1 | 1 | Low |
| 3. | Delete Book | 1 | 1 | Low |
| 4. | Check Member’s Record | 1 | 1 | Low |
| 5. | Check Book’s Detail | 1 | 1 | Low |
ILF
| S. No | File Name | No. of fields | No. of records | Complexity |
| 1. | Member’s Record | 14 | 1 | Low |
| 2. | Book’s Record | 8 | 1 | Low |
| 3. | Staff Record | 10 | 1 | Low |
FPA Calculation
Unadjusted Functional Point Calculation
| Simple | Average | Complex | Total | |
| No. of inputs | 2*3 | 5*4 | 0*6 | 26 |
| No. of outputs | 0*4 | 4*5 | 0*7 | 20 |
| No. of files | 3*7 | 0*10 | 0*15 | 21 |
| No. of queries | 5*3 | 0*4 | 0*6 | 15 |
| UFP | 82 |
Function Point Calculation
FP= UFP * ( 0.65 + 0.01 * åFi )
= 82 * ( 0.65 + 0.01 * 42)
= 82 * 1.07
= 87.74
Requirement Analysis & Management
Introduction
This is the process of deriving system requirements through observation of the existing system, discussions with potential users, task analysis and so on. This may involve the development of one or more different system model. These help the analyst to understand the system to be more specific.
Requirement Analysis
Requirement analysis is a software engineering task that bridges the gap between system level requirements engineering and software design.
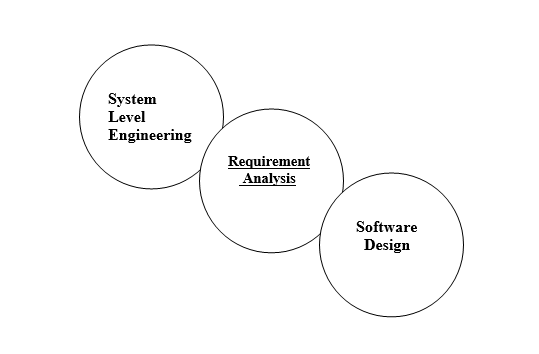
The software requirements analysis may be divided into five areas of efforts:-
Problem recognition
Recognition of basic problem elements as perceived by the users.
Evaluation and synthesis
Define all data objects, evaluate the flow and content of information, define and elaborate all functions, understand software behavior and establish interface characteristics.
Modeling
Functional models represent the information that software transforms, functions enabling the transformation, and behavior of the system during transformation.
Specification
States the goals and objectives of the software, describing it in context of the
Computer-based system.
Review
Changes to the specification may be recommended.
Analysis Principles
- The information domain of a problem must be represented and understood.
- The functions to be performed by software must be defined.
- The behavior of the software must be represented.
- The models that depict information function and behavior must be partitioned in a manner that uncovers detail in a layered fashion.
- The analysis process should move from essential information towards implementation detail.
Non-Functional Requirements
(1) The server must have enough disk space so as to store a large amount of data.
(2) The system should provide data security. Unauthorized users should not be allowed to access the system so that the integrity and secrecy of each client must be maintained.
(3) A network operating system that can support the software.
Functional Requirements
(1) The system must be easy to learn and easy to use so that it is readily accepted by its prospective users. It must provide easy and convenient means of communication between different clients.
(2) It should synchronize the access of channels to clients. No two clients should be allowed to transmit data simultaneously.
(3) It must detect collisions and recover lost messages.
(4) The client should not be allowed to run while the server is not running.
(5) It must handle exceptional conditions appropriately and efficiently.
(6) Appropriate error messages should be generated in case some exception has occurred.
(7) It must support client-to-client communication as well as broadcasting.
(8) The system must be fault tolerant i.e. it can continue in operation even after some system failure has occurred.
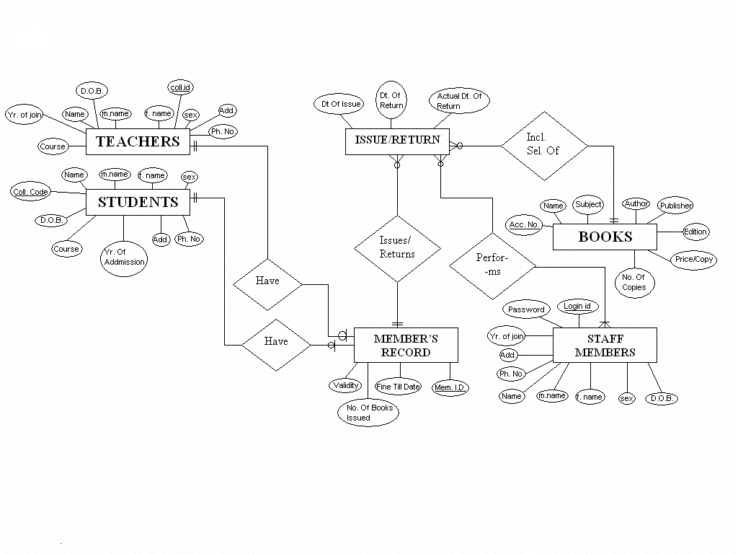
Data Dictionary
| S. No. | Data Item | Type | Length | Description |
|
1 |
TEACHERS |
|||
|
1.1 |
Name |
String |
30 |
Contains Name of the teacher |
|
1.2 |
F. Name |
String |
30 |
Contains Father’s Name of the teacher |
|
1.3 |
M. Name |
String |
30 |
Contains Mother’s Name of the teacher |
| 1.4 | D.O.B. | Integer | 10 | Date of Birth |
| 1.5 | Sex | String | 6 | Sex Of the teacher |
| 1.6 | Add. | String | 50 | Residential Address |
| 1.7 | Ph. No. | Integer | 10 | Contact Number |
|
1.8 |
Subject |
String |
10 |
Subject taught by the teacher |
| 1.9 | Coll. I.D. | Integer | 10 | College I.D. No. |
| 1.10 | Yr. Of Join | Integer | 4 | Year of joining |
|
2 |
STUDENTS |
|||
|
2.1 |
Name |
String |
30 |
Contains Name of the student |
|
2.2 |
F. Name |
String |
30 |
Contains Father’s Name of the student |
|
2.3 |
M. Name |
String |
30 |
Contains Mother’s Name of the student |
| 2.4 | D.O.B. | Integer | 10 | Date of Birth |
| 2.5 | Sex | String | 6 | Sex Of the student |
| 2.6 | Add. | String | 50 | Residential Address |
| 2.7 | Ph. No. | Integer | 10 | Contact Number |
|
2.8 |
Course |
String |
10 |
Course chosen by the student |
|
2.9 |
Coll. Code |
Integer |
10 |
College Code of the student |
| 2.10 | Yr. Of Admission | Integer | 4 | Year of admission |
|
3 |
ISSUE / RETURN |
|||
| 3.1 | Dt. Of Issue | Integer | 10 | Date of issue |
| 3.2 | Dt. Of Return | Integer | 10 | Date of return |
| 3.3 | Actual Dt. Of Return | Integer | 10 | Actual Date of return |
|
4 |
MEMBER’S RECORD
|
|||
| 4.1 | Member I.D. | Integer | 10 | Member’s I.D. No. |
|
4.2 |
No. Of Books Issued |
Integer |
1 |
Number of books issued on member’s account |
|
4.3 |
Validity |
Integer |
4 |
Date of expiry of membership |
|
4.4 |
Fine Till Date |
Integer |
4 |
Fine to be paid till present date |
|
5 |
BOOKS
|
|||
|
5.1 |
Name |
String |
30 |
Contains Name of the book |
|
5.2 |
Author |
String |
30 |
Contains Author’s Name of the book |
|
5.3 |
Publisher |
String |
30 |
Contains Publisher’s Name of the book |
| 5.4 | Edition | Integer | 2 | Edition of the book |
|
5.5 |
No. Of Copies |
Integer |
3 |
No. of copies available of the book |
|
5.6 |
Price/Copy |
Integer |
4 |
Price per copy of the book |
| 5.7 | Acc. No. | Integer | 10 | Acc. Number of the book |
|
5.8 |
Subject |
String |
20 |
Subject related to the book |
|
6 |
LIBRARY STAFF
|
|||
|
6.1 |
Name |
String |
30 |
Contains the Name of the staff member |
|
6.2 |
F. Name |
String |
30 |
Contains Father’s Name of the staff member |
|
6.3 |
M. Name |
String |
30 |
Contains Mother’s Name of the staff member |
| 6.4 | D.O.B. | Integer | 10 | Date of Birth |
| 6.5 | Sex | String | 6 | Sex Of the staff member |
| 6.6 | Add. | String | 50 | Residential Address |
| 6.7 | Ph. No. | Integer | 10 | Contact Number |
| 6.8 | Yr. Of Join | Integer | 4 | Year of joining |
|
6.9 |
Login I.D. |
String |
20 |
Login I.D. of the staff member |
|
6.10 |
Password |
String |
20 |
Password of the staff member |
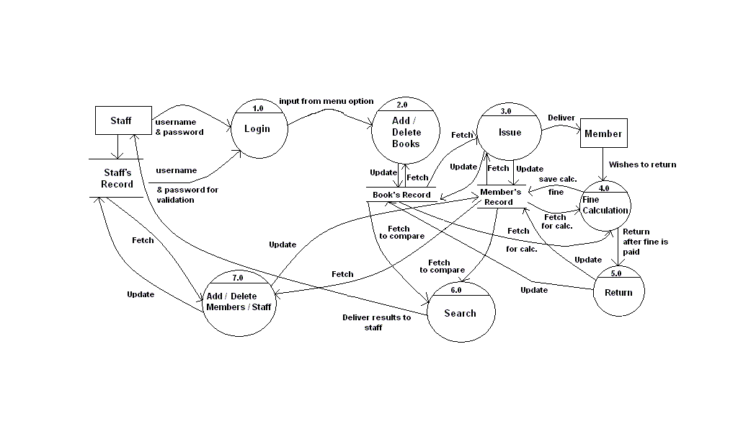
Entity Relationship and Data Flow Diagram

Design Concepts & Principles
The design is a meaningful engineering representation of something that is to be built. It can be traced to customer’s requirements and at the same time assessed for good quality against a set of predefined criteria for a “Good Design”.
Software Design is applied regardless of the software process model that is used. Once software requirements have been analyzed and specified, software design is the first of three technical activities – design, code generation, and test – that are required to build and verify the software.
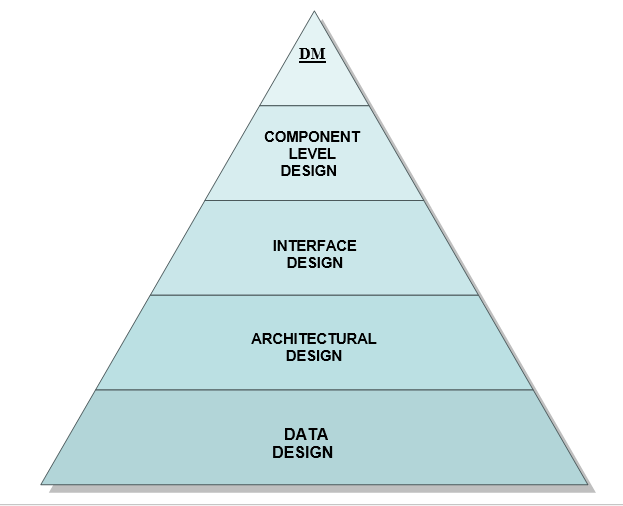
The design focuses on four major areas of concern: data, architecture, interfaces, and components.
Component Level Design
It transforms structural elements of software architecture into a procedural description of software components.
Interface Design
It describes how the software communicates within itself, with systems that interoperate with it, and with the users who use it.
Architectural Design
It defines the relationship between major structural elements of the software.
Data Design
It transforms the information domain model created during analysis into the data structures that will be required to implement the software.
Design Model
Database Design
Teachers
| S.No. | Data Item | Type | Length | Description | Mandatory/
Optional |
Primary Key |
|
1.1 |
Name |
String |
30 |
Contains Name of the teacher |
M |
– |
|
1.2 |
F.Name |
String |
30 |
Contains Father’s Name of the teacher |
O |
– |
|
1.3 |
M.Name |
String |
30 |
Contains Mother’s Name of the teacher |
O |
– |
| 1.4 | D.O.B. | Integer | 10 | Date of Birth | O | – |
| 1.5 | Sex | String | 6 | Sex Of the teacher | M | – |
| 1.6 | Add. | String | 50 | Residential Address | O | – |
| 1.7 | Ph. No. | Integer | 10 | Contact Number | O | – |
|
1.8 |
Subject |
String |
10 |
Subject taught by the teacher |
M |
– |
| 1.9 | Coll.I.D. | Integer | 10 | College I.D. No. | M | YES |
| 1.10 | Yr. Of Join | Integer | 4 | Year of joining | O | – |
Students
| S.No. | Data Item | Type | Length | Description | Mandatory/
Optional |
Primary Key |
|
2.1 |
Name |
String |
30 |
Contains Name of the student |
M |
– |
|
2.2 |
F.Name |
String |
30 |
Contains Father’s Name of the student |
O |
– |
|
2.3 |
M. Name |
String |
30 |
Contains Mother’s Name of the student |
O |
– |
| 2.4 | D.O.B. | Integer | 10 | Date of Birth | O | – |
| 2.5 | Sex | String | 6 | Sex Of the student | M | – |
| 2.6 | Add. | String | 50 | Residential Address | O | – |
|
2.7 |
Ph. No. |
Integer |
10 |
Contact Number |
O |
– |
|
2.8 |
Course |
String |
10 |
Course chosen by the student |
M |
– |
|
2.9 |
Coll. Code |
Integer |
10 |
College Code of the student |
M |
YES |
| 2.10 | Yr. Of Admission | Integer | 4 | Year of admission | O | – |
Issue / Return
| S.No. | Data Item | Type | Length | Description | Mandatory/
Optional |
Primary Key |
| 3.1 | Dt. Of Issue | Integer | 10 | Date of issue | M | – |
| 3.2 | Dt. Of Return | Integer | 10 | Date of return | M | – |
|
3.3 |
Actual Dt. Of Return |
Integer |
10 |
Actual Date of return |
M |
– |
Member’s Record
| S.No. | Data Item | Type | Length | Description | Mandatory/
Optional |
Primary Key |
| 4.1 | Member I.D. | Integer | 10 | Member’s I.D. No. | M | YES |
|
4.2 |
No. Of Books Issued |
Integer |
1 |
Number of books issued on member’s account |
M |
– |
|
4.3 |
Validity |
Integer |
4 |
Date of expiry of membership |
M |
– |
|
4.4 |
Fine Till Date |
Integer |
4 |
Fine to be paid till present date |
M |
– |
Books
| S.No. | Data Item | Type | Length | Description | Mandatory/
Optional |
Primary Key |
|
5.1 |
Name |
String |
30 |
Contains Name of the book
|
M |
– |
|
5.2 |
Author |
String |
30 |
Contains Author’s Name of the book |
M |
– |
|
5.3 |
Publisher |
String |
30 |
Contains Publisher’s Name of the book |
M |
– |
| 5.4 | Edition | Integer | 2 | Edition | M | – |
|
5.5 |
No. Of Copies |
Integer |
3 |
No. of copies available |
O |
– |
|
5.6 |
Price/Copy |
Integer |
4 |
Price per copy of the book |
O |
– |
|
5.7 |
Acc. No. |
Integer |
10 |
Acc. Number of the book |
M |
YES |
|
5.8 |
Subject |
String |
20 |
Subject related to the book |
M |
– |
Library Staff
| S.No. | Data Item | Type | Length | Description | Mandatory/
Optional |
Primary Key |
|
6.1 |
Name |
String |
30 |
Contains Name of the staff member |
M |
– |
|
6.2 |
F.Name |
String |
30 |
Contains Father’s Name of staff the member |
O |
– |
|
6.3 |
M.Name |
String |
30 |
Contains Mother’s Name of the staff member |
O
|
– |
| 6.4 | D.O.B. | Integer | 10 | Date of Birth | O | – |
|
6.5 |
Sex |
String |
6 |
Sex Of the staff member |
M |
– |
| 6.6 | Add. | String | 50 | Residential Address | O | – |
| 6.7 | Ph. No. | Integer | 10 | Contact Number | O | – |
| 6.8 | Yr. Of Join | Integer | 4 | Year of joining | M | – |
|
6.9 |
Login I.D. |
String |
20 |
Login I.D. of staff member |
M |
YES |
|
6.10 |
Password |
String |
20 |
Password of the staff member |
M |
– |
Pseudo Code
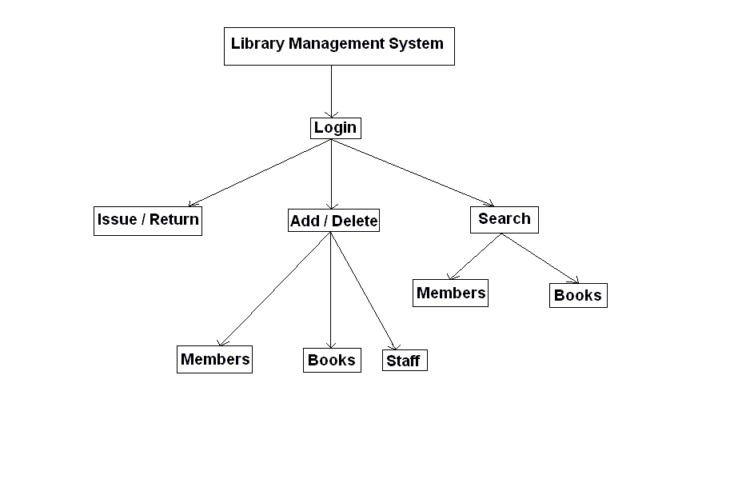
Login Screen
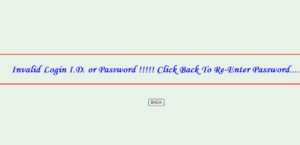
This screen takes the unique login-id & password of the library staff member allowing him/her to use the system at his/her level of interference.
Menu Screen
This screen asks the library staff member to input the choice of tasks he/she wants to perform. Choices include- Add/Delete a member, Add/Delete a book, Search for a member/book, Check the details of a particular member/book, Issue/Return a book etc.
Add a new member
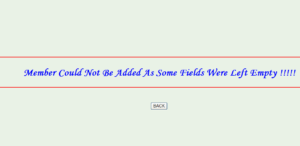
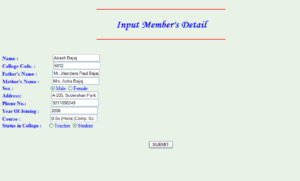
This screen takes the details of the new member to be added from the library staff & then accepts the new member as a part of the library unless & until some fields are not left empty or are given invalid inputs. Details include- Name, Father’s name, Mother’s name, Sex, Address, Phone No., College code, Year of joining/Admission, Status in the college (whether Student or Teacher), Course etc.
Delete a member
This screen takes the member’s id of the member to be deleted as the input from the library staff & then deletes the member from the library records unless an invalid member id is not entered by the staff member.
Add a new book
This screen takes the details of the new book to be added from the library staff & then makes the new book available for Issue/Return unless & until some fields are not left empty or are given invalid inputs. Details include- Name, Author’s name, Publisher’s name, Edition, No. of copies, Price per copy, Acc. No., Subject etc.
Delete a book
This screen takes the Acc. No. of the book to be deleted as the input from the library staff & then deletes the book from the library records unless an invalid Acc. No. is not entered by the staff member. The book deleted no longer remains available for Issue/return purposes.
Search for a member
This screen takes some description about the member to be searched according to the method of searching chosen by the library staff member. The methods of searching include- Search by name, by course, by member id etc. The records found are displayed on the same screen (if they really exist). This screen also allows the staff member to select a name from the records found & then check the details of the member directly from here.
Check member details
This screen takes the member id as the input from the library staff member & then searches for the member among a list of members and then displays the full details of the member searched if a valid member id is provided as the input. This screen also allows the library staff to issue this member a book directly from this screen as the staff member doesn’t need to enter the member id while issuing the book. The book is issued unless the member’s account is not full (max. of 5 books is taken as an assumption) or an invalid Acc. No. is not added.
Search for a book
This screen takes some description about the book to be searched according to the method of searching chosen by the library staff member. The methods of searching include- Search by name, by subject, by author etc. The records found are displayed on the same screen (if they really exist). This screen also allows the staff member to select a book from the records found & then check the details of the book directly from here.
Checkbook detail
This screen takes the Acc. No. as the input from the library staff member & then searches for the book among a list of books and then displays the full details of the book searched if a valid Acc. No. is provided as the input. This screen also allows the library staff to issue this book directly to a member from this screen as the staff member doesn’t need to enter the Acc. No. while issuing the book. The book is issued unless the member’s account is not full (max. of 5 books is taken as an assumption) or an invalid member id is not added.
Issue
This screen takes member id, Acc. No., Date of issue, Date of return from the library staff & then issues the selected book the member unless an invalid member id or Acc. No. is not entered by the staff member or the member’s account is not full (max. of 5books is taken as an assumption) or else the book is not already issued to some other member.
Return
This screen takes the member id, Acc. No. as the input from the library staff & then displays the details of the book. The details include- Date of issue, Date of return. Date of actual return is entered by the staff member & the fine is calculated if the Actual date of return is later than the Date of return specified to the member. The book is then deleted from the member’s account when all dues are cleared and it is again available for issue/return purposes.
Architectural Design
Interface Design







Leave A Comment
You must be logged in to post a comment.