Laundry Management System Capstone Project Document
Intoduction
Laundry System project is developed using PHP, CSS and JavaScript. Talking about the project, it has all the essential features. This project has an administration side from Where he/she can view all the laundry, manage laundry type, generate report and change password. In this project, all the functions are performed from the Admin side which means there is no user side.
There are mainly 3 modules in this software
- Laundry type module
- Customer Module
- Sales Report Module
Admin has full control of the system, he/she can view all the laundry, claim it, manage the laundry type, generate report and change password. He/she can add, edit, delete, claim Laundry. While adding Laundry items, he/she has to provide Customer name, Priority number, laundry weight and select laundry type. Likewise while adding Laundry type, he/she has to provide Laundry type name and Price per kilo. To claim a laundry, the user has to select the respective laundry and click the Claim button, the system automatically generates the total amount of the customer. After claiming it, he/she can print the report too. Laundry System helps in easy management of Laundry in a Laundry shop as it is not time-consuming.
Another feature is that the user can change the password by entering New Password and Confirm Password from the Change Password Settings. A simple dashboard is provided in the admin panel for the easy management of the system. Design of this project is pretty and responsive so that user won’t find it difficult to understand, use and navigate.
System Analysis
System analysis is the detailed study of various operations performed by a system and their relationships within and outside of the system.Here the key question is –what all problems exist in the present system?What must be done to solve the problem?
Analysis begins when a user or manager begins a study of the program using existing system.
Existing System:
Laundry firm currently uses a manual system for the management and maintenance of critical information. The current system requires numerous paper forms, with data stores spread throughout the Laundry firm management infrastructure. Often informationsis incomplete, or does not follow management standards. Forms are often lost in transit between departments requiring a comprehensive auditing process to ensure that no vital information is lost. This has leads to inconsistencies in various data due to large volume of contrasting customer details leading to mix-up of clothes in the laundry firm whichthus leads to delay in collecting the clothes back
Proposed System:
The Laundry Management System is designed for any Laundry firm to replace their existing manual, paper based system. These services are to be provided in an efficient, cost effective manner, with the goal of reducing the delay and resources currently required for such tasks as clothes details are bounded by customer name . Since the existing system makes use of tedious administrative tasks, lots paper work and time, in which full information cannot be gotten from busy customers.
The goal of the laundry database management system is to provide a computerized process that is stress free, reliable PHP would be at the front-end and provide the graphical user interface that relates with the user, while the SQL database will be at the back-end to handle the data storage process.
- Administrative Side
- Add New Laundry Types
- Add, Edit, View and Delete Laundry
- Claim Laundry
- Change Password
- Generate Report
Feasiblity Analysis
Whatever we think need not be feasible.it is wise to think about the about the feasibility of any problem we undertake.Feasibility is the study of impact, which happens in the organization by the development of a system.The impact can be either positive or negative.When the positive nominate the negative,then the system is considered feasibility study can be performed in two ways such as technical feasibility andeconomical feasibility.
Technical Feasibility:
We can strongly says that it is technically feasible,since there will not be much difficulty in getting required resources for the development and maintenances of the same is available in the organization here we are utilizing the resources which are available already.
Operational Feasibility:
Operational feasibility refers to the measure of solving problems with the help of a new proposed system. It helps in taking advantage of the opportunities and fulfills the requirements as identified during the development of the project. It takes care that the management and the users support the project.
Economical Feasibility:
Development of this application is highly economically feasible .The organization needed not spend much money for the development of the system already available .The only thing is to be done is making an environment for the development with an effective supervision.If we are doing so,we are attain the maximum usability of the corresponding resources.Even after development,the organization will not be in condition to invest more in the organization.
Therefore,the system is economically feasible.
Operating Environment
Hardware Configuration
Processor : Pentium IV 800 MHz
Memory size : 512 MB RAM
Storage : 20 GB Hard Disk
Display : VGA,LCD,LED Color Monitor600 x 800 Pixels Resolution High Color (16 Bit)
Key Board : Any with required all keys
Mouse : Any
Network: :Intranet.
Software Configuration
Operating System: Windows
Application Server : Apache Tomcat.
Front End: HTML-5, CSS-3.
Scripts: JavaScript
Server side Script: PHP.
Database: Mysql.
Database Connectivity: PDO(PHP Data objects)
Browser: Google chrome, Mozilla Firefox .
Software Requirementspecification(Srs)
Purpose: The main purpose for preparing this document is to give a general insight into the analysis and requirements of the existing system or situation and for determining the operating characteristics of the system.
Scope: This Document plays a vital role in the development life cycle (SDLC) and it describes the complete requirement of the system. It is meant for use by the developers and will be the basic during testing phase. Any changes made to the requirements in the future will have to go through formal change approval process
Functional Requirements
Input Design
Input design is a part of overall system design. The main objective during the input design is as given below:
- To produce a cost-effective method of input.
- To achieve the highest possible level of accuracy.
- To ensure that the input is acceptable and understood by the user.
INPUT STAGES:
The main input stages can be listed as below:
- Data recording.
- Data transcription.
- Data conversion.
- Data verification.
- Data control.
- Data transmission.
- Data validation.
- Data correction.
INPUT TYPES:
It is necessary to determine the various types of inputs can be categorized as follows:
- External inputs, which are prime inputs for the system.
- Internal inputs, which are user communications with the system.
- Operational, which are computer department’s communications to the system?
- Interactive, which are inputs entered during a dialogue.
INPUT MEDIA:
At this stage choice has to be made about the input media. To conclude about the input media consideration has to be given to;
- Type of input.
- Flexibility of format.
- Verification methods.
- Rejection rates.
- Ease of correction.
- Storage and handling requirements.
- Easy to use.
Keeping in view the above description of the input types and input media, it can be said that most of the inputs are of the form of internal and interactive. As Input data is to be the directly keyed in by the user, the keyboard can be considered to be the most suitable input device.
ERROR AVOIDANCE
At this stage care is to be taken to ensure that input data remains accurate form the stage at which it is recorded up to the stage in which the data is accepted by the system. This can be achieved only by means of careful control each time the data is handled.
ERROR DETECTION
Even though every effort is make to avoid the occurrence of errors, still a small proportion of errors always likely to occur, these types of errors can be discovered by using validations to check the input data.
Output Design
Outputs from computer systems are required primarily to communicate the results of processing to users. They are also used to provide a permanent copy of the results for later consultation. The various types of outputs in general are:
- External Outputs, whose destination is outside the organization.
- Internal Outputs whose destination is within organization .
- User’s main interface with the computer.
- Operational outputs whose use is purely within the computer department.
OUTPUT DEFINITION
The outputs should be defined in terms of the following points:
- Type of the output.
- Content of the output.
- Format of the output.
- Location of the output.
- Frequency of the output.
- Volume of the output.
- Sequence of the output.
It is not always desirable to print or display data as it is held on a computer. It should be decided as which form of the output is the most suitable.
For Example
- Will decimal points need to be inserted
- Should leading zeros be suppressed.
OUTPUT MEDIA
In the next stage it is to be decided that which medium is the most appropriate for the output. The main considerations when deciding about the output media are:
- The suitability for the device to the particular application.
- The need for a hard copy.
- The response time required.
- The location of the users.
- The software and hardware available.
Keeping in view the above description the project is to have outputs mainly coming under the category of internal outputs. The main outputs desired according to the requirement specification are:
The outputs were needed to be generated as a hot copy and as well as queries to be viewed on the screen. Keeping in view these outputs, the format for the output is taken from the outputs, which are currently being obtained after manual processing. The standard printer is to be used as output media for hard copies.
Database Design
The general theme behind a database is to handle information as an integrated whole.
A database is a collection of interrelated data stored with minimum redundancy to serve many users quickly & effectively . After designing input &output,the analyst must concentrate on database design or how data should be organized around user requirements. The general objective is to make information access, easy quick, inexpensive & flexible for other users. During database design the following objectives are concerned :-
- Controlled redundancy
- Data independence
- Accurate & integrating
- More information at low cost
- Recovery from failure
- Privacy & security
- Performance
- Ease of learning & use.
Performance Requirements
Performance is measured in terms of the output provided by the application. Requirement specification plays an important part in the analysis of a system. Only when the requirement specifications are properly given, it is possible to design a system, which will fit into required environment. It rests largely in the part of the users of the existing system to give the requirement specifications because they are the people who finally use the system. This is because the requirements have to be known during the initial stages so that the system can be designed according to those requirements. It is very difficult to change the system once it has been designed and on the other hand designing a system, which does not cater to the requirements of the user, is of no use.
- The requirement specification for any system can be broadly stated as given below:
- The system should be able to interface with the existing system
- The system should be accurate
- The system should be better than the existing system
System Design
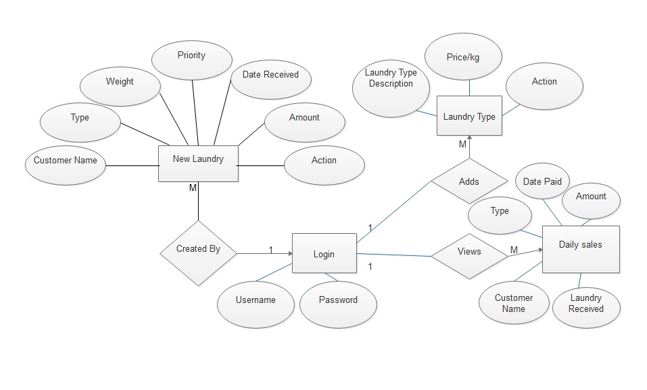
E-R Diagram
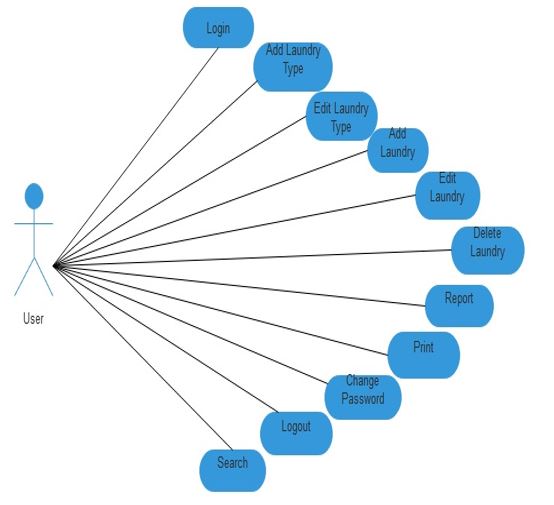
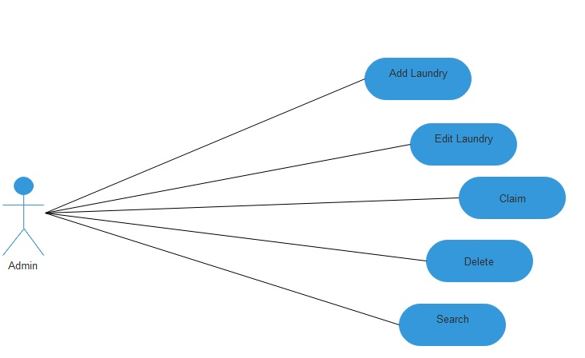
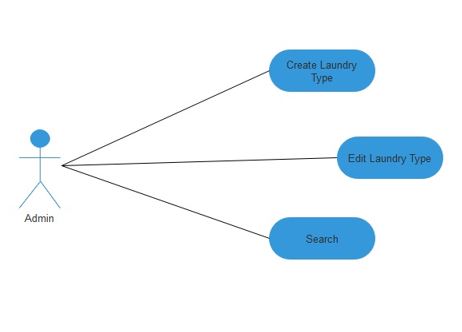
Use Case Diagram
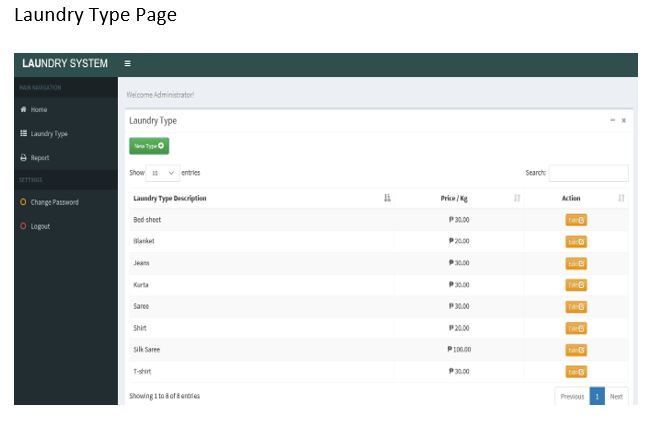
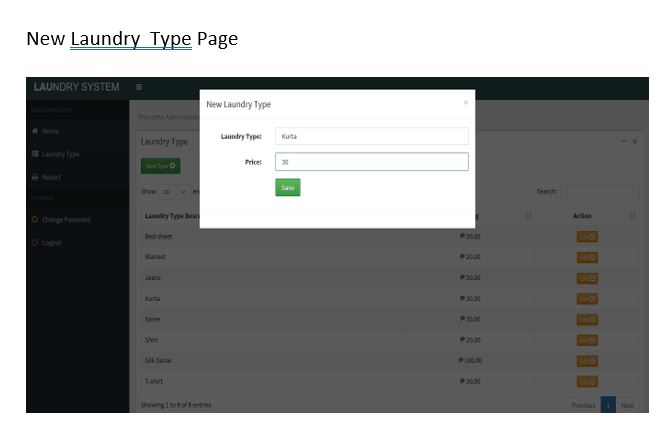
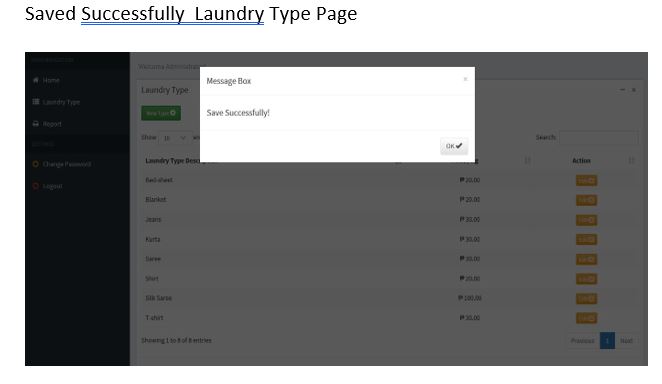
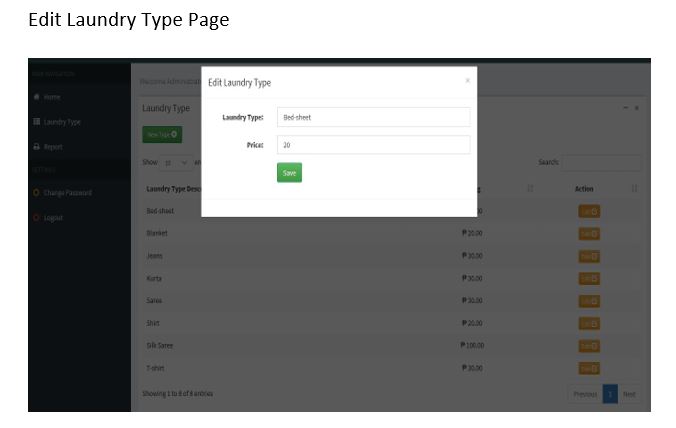
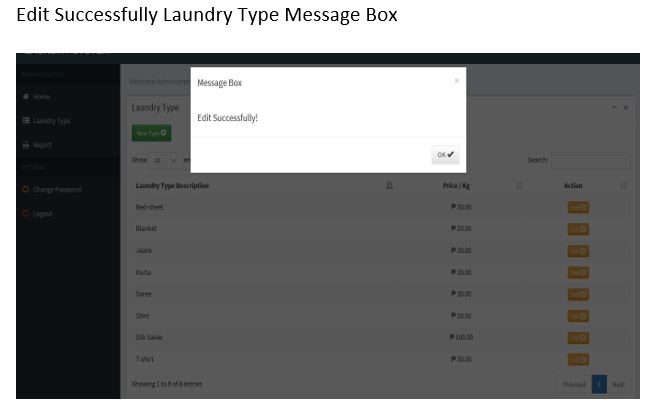
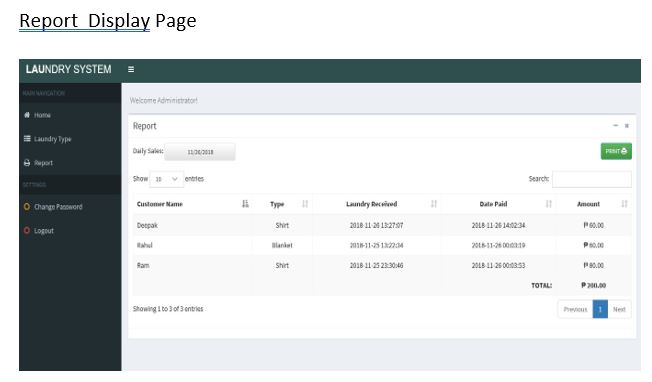
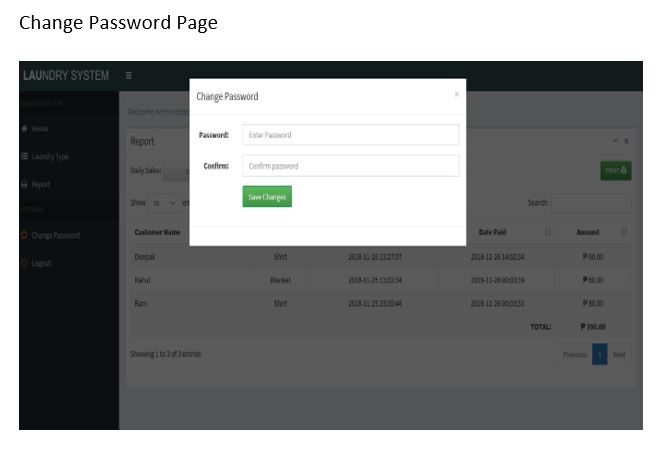
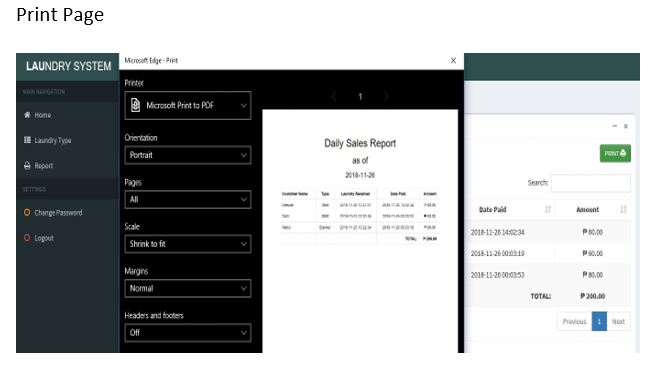
Screen Shots
System Testing And Implementation
Introduction
Software testing is a critical element of software quality assurance and represents the ultimate review of specification, design and coding. In fact, testing is the one step in the software engineering process that could be viewed as destructive rather than constructive.
A strategy for software testing integrates software test case design methods into a well-planned series of steps that result in the successful construction of software. Testing is the set of activities that can be planned in advance and conducted systematically. The underlying motivation of program testing is to affirm software quality with methods that can economically and effectively apply to both strategic to both large and small-scale systems.
Strategic Approach To Software Testing
The software engineering process can be viewed as a spiral. Initially system engineering defines the role of software and leads to software requirement analysis where the information domain, functions, behavior, performance, constraints and validation criteria for software are established. Moving inward along the spiral, we come to design and finally to coding. To develop computer software we spiral in along streamlines that decrease the level of abstraction on each turn.
A strategy for software testing may also be viewed in the context of the spiral. Unit testing begins at the vertex of the spiral and concentrates on each unit of the software as implemented in source code. Testing progress by moving outward along the spiral to integration testing, where the focus is on the design and the construction of the software architecture. Talking another turn on outward on the spiral we encounter validation testing where requirements established as part of software requirements analysis are validated against the software that has been constructed. Finally we arrive at system testing, where the software and other system elements are tested as a whole.
Unit Testing
Unit testing focuses verification effort on the smallest unit of software design, the module. The unit testing we have is white box oriented and some modules the steps are conducted in parallel.
- WHITE BOX TESTING
This type of testing ensures that
- All independent paths have been exercised at least once
- All logical decisions have been exercised on their true and false sides
- All loops are executed at their boundaries and within their operational bounds
- All internal data structures have been exercised to assure their validity.
To follow the concept of white box testing we have tested each form .we have created independently to verify that Data flow is correct, All conditions are exercised to check their validity, All loops are executed on their boundaries.
- CONDITIONAL TESTING
In this part of the testing each of the conditions were tested to both true and false aspects. And all the resulting paths were tested. So that each path that may be generate on particular condition is traced to uncover any possible errors.
- DATA FLOW TESTING
This type of testing selects the path of the program according to the location of definition and use of variables. This kind of testing was used only when some local variable were declared. The definition-use chain method was used in this type of testing. These were particularly useful in nested statements.
- LOOP TESTING
In this type of testing all the loops are tested to all the limits possible. The following exercise was adopted for all loops:
- All the loops were tested at their limits, just above them and just below them.
- All the loops were skipped at least once.
- For nested loops test the inner most loop first and then work outwards.
- For concatenated loops the values of dependent loops were set with the help of connected loop.
- Unstructured loops were resolved into nested loops or concatenated loops and tested as above.
Test Plan
A Software Test Plan is a document describing the testing scope and activities. It is the basis for formally testing any software/product in a project, Test Plans are comprehensive evaluation of programs, and procedures.
Test Plans: Plans for each level of testing.
- Black Box Testing
- Program Testing/ Unit Testing
- System Testing
- Parallel Testing
Black Box Testing:
In this testing functional design of the system will be checked, without regard to the internal program structure.
Unit Testing:
In the testing individual programs are checked to extend of desired output i.e. program specifications. While checking boundary conditions, exceptional Handling, error Handling etc.
Integration Testing:
It is the process of combining and multiple components together. To assure that the software units or components operate properly when combined together
System Testing:
These are used to test all program, which together constitute the system.the system testing is conducted using synthetic data both valid and invalid transaction are used in this test.
The step used in the system testing is:
- Decompose and analyze the requirement specification.
- Partition the requirements into logical categories and for each component make a list of the detailed requirements.
System Security
Introduction
The protection of computer based resources that includes hardware, software, data, procedures and people against unauthorized use or natural disaster is known as System Security.
System Security can be divided into four related issues:
- Security
- Integrity
- Privacy
- Confidentiality
SYSTEM SECURITY:- Refers to the technical innovations and procedures applied to the hardware and operation systems to protect against deliberate or accidental damage from a defined threat.
DATA SECURITY:-It is the protection of data from loss, disclosure, modification and destruction.
SYSTEM INTEGRITY:-Refers to the power functioning of hardware and programs, appropriate physical security and safety against external threats such as eavesdropping and wiretapping.
PRIVACY:-Defines the rights of the user or organizations to determine what information they are willing to share with or accept from others and how the organization can be protected against unwelcome, unfair or excessive dissemination of information about it.
CONFIDENTIALITY:-It is a special status given to sensitive information in a database to minimize the possible invasion of privacy. It is an attribute of information that characterizes its need for protection.
Security In Software
System security refers to various validations on data in form of checks and controls to avoid the system from failing. It is always important to ensure that only valid data is entered and only valid operations are performed on the system. The system employees two types of checks and controls.
CLIENT SIDE VALIDATION
Various client side validations are used to ensure on the client side that only valid data is entered. Client side validation saves server time and load to handle invalid data. Some checks imposed are:
- Forms cannot be submitted without filling up the mandatory data so that manual mistakes of submitting empty fields that are mandatory can be sorted out at the client side to save the server time and load.
- Tab-indexes are set according to the need and taking into account the ease of user while working with the system.
SERVER SIDE VALIDATION
Some checks cannot be applied at client side. Server side checks are necessary to save the system from failing and intimating the user that some invalid operation has been performed or the performed operation is restricted. Some of the server side checks imposed is:
- Server side constraint has been imposed to check for the validity of primary key and foreign key. A primary key value cannot be duplicated. Any attempt to duplicate the primary value results into a message intimating the user about those values through the forms using foreign key can be updated only of the existing foreign key values.
- User is intimating through appropriate messages about the successful operations or exceptions occurring at server side.
- Various Access Control Mechanisms have been built so that one user may not agitate upon another. Access permissions to various types of users are controlled according to the organizational structure. Only permitted users can log on to the system and can have access according to their category. User- name, passwords and permissions are controlled o the server side.
- Using server side validation, constraints on several restricted operations are imposed.
Conclusion
It has been a great pleasure for me to work on this exciting and challenging project. This project proved good for me as it provided practical knowledge of not only programming in HTML5, CSS, Javascript, PHP based application and know some extent Apache Tomcat Server, but also about all handling procedure related with “LAUNDRY DATABASE MANAGEMENT SYSTEM ”. It also provides knowledge about the latest technology used in developing application and client server technology that will be great demand in future. This will provide better opportunities and guidance in future in developing projects independently.
The application is useful for maintaining organization in computerized way. It contains some limitation which we would like to enhance it in our next tasks and try to overcome them.





Leave A Comment
You must be logged in to post a comment.